
Imperva SecureSphere - Database Assessment
Vulnerability Assessment and Configuration Audit
Overview:
You can’t protect against problems if you don’t know they exist. For example, organizations can be blindsided by a breach of production data copied to unmanaged testing servers. SecureSphere solves this by quickly identifying sensitive data, database vulnerabilities and misconfigurations so that you can prioritize and mitigate them. Database Assessment helps you stay out of the headlines by ensuring that database protection conforms to regulations, best practices, and a company’s internal standards.
SecureSphere Database Assessment identifies database vulnerabilities and measures compliance with industry standards and best practices. Combined with sensitive data discovery and data classification, organizations can accurately scope security and compliance projects and prioritize risk mitigation efforts.

Key Capabilities :
- Detect database vulnerabilities based on the latest research by Imperva ADC
- Audit configurations and measure compliance with industry standards and best practices
- Identify databases that contain sensitive data, surface "rogue" databases
- Virtually Patch vulnerabilities via integration with SecureSphere Database Firewall (DBF)
- Calculate the risk to data based on data sensitivity and the severity of vulnerabilities
Features:
Vulnerability Assessment: Detect Exposed Databases
SecureSphere Database Assessment provides a comprehensive list of over 1500 tests and assessment policies for scanning platform, software, and configuration vulnerabilities. The vulnerability assessment process, which can be fully customized, uses industry best practices such as DISA STIG and CIS benchmarks. It results in a set of detailed reports documenting vulnerabilities that put databases at risk, as well as configurations that deviate from defined standards.
Virtual Patching: Protect Before Patches Are Available
SecureSphere Database Assessment enables protection against attempts to exploit vulnerabilities when deployed with SecureSphere Database Firewall (DBF). Customers can enable real-time security policies to block or alert on attempts to exploit vulnerabilities. This allows for immediate protection while patches are developed by the software vendors, thoroughly tested and safely deployed on the database servers.
Discovery and Classification: Locate Sensitive Data
SecureSphere Database Assessment identifies where databases are located on the network and surfaces "rogue" databases. SecureSphere scans the databases for sensitive data that is the focus of security and compliance projects. The results highlight wellknown and custom sensitive data types, and track their location down to the database object, row and column. Object and column level classification enables organizations to focus on data in scope for security and compliance projects and configure granular policies to reduce the resource impact of these projects.

User Rights Management: Find Excessive Rights
SecureSphere Database Assessment enables automatic aggregation and review of user rights with the User Rights Management for Databases (URMD) add-on option. SecureSphere supports a focused analysis of rights to sensitive data and identification of excessive rights and dormant accounts based on organizational context, object sensitivity and actual usage. Using URMD organizations can demonstrate compliance with regulations such as SOX, PCI 7, and PCI 8.5 and reduce the risk of data breach.
Database Auditing and Protection: the Next Step for Data Security
For complete visibility and control of user access to sensitive data, SecureSphere Database Assessment can be extended to include database activity auditing (DAM). Combining SecureSphere Database Assessment and DAM enables administrators to define and deploy granular, focused audit policies making this powerful solution more effective and easier to use.
Data Risk Analysis: Putting it All Together
SecureSphere Database Assessment enables educated decision making by providing a combined analysis of vulnerabilities and affected sensitive data. SecureSphere calculates the risk associated with each data asset based on data sensitivity and the severity of platform and database vulnerabilities. A graphical dashboard with drill down capabilities supports risk-focused prioritization of risk reduction efforts.
Deployment:
Unparalleled Database Security and Compliance
SecureSphere addresses all aspects of database security and compliance with industry-best database auditing and real-time protection that will not impact performance or availability. With its multi-tier architecture, SecureSphere scales to support the largest database installations. By automating security and compliance, it is not surprising that thousands of organizations choose Imperva SecureSphere to safeguard their most valuable assets.
- Non-inline Network Monitoring: Activity monitoring with zero impact on database performance or availability
- Transparent Inline Protection: Drop-in deployment and industry-best performance
- Agent-based Monitoring and Blocking: Lightweight software agents that monitor and block direct privileged activities and network traffic
- Gateway Clustering: Cost-effective resilient database auditing
- Supported Database Platforms: Oracle, Oracle Exadata, Microsoft SQL Server, IBM DB2 (on Linux, UNIX, Windows, z/OS and DB2/400), IBM IMS on z/OS, IBM Informix, IBM Netezza, SAP Sybase, Teradata, Oracle MySQL, PostgreSQL, and Progress OpenEdge
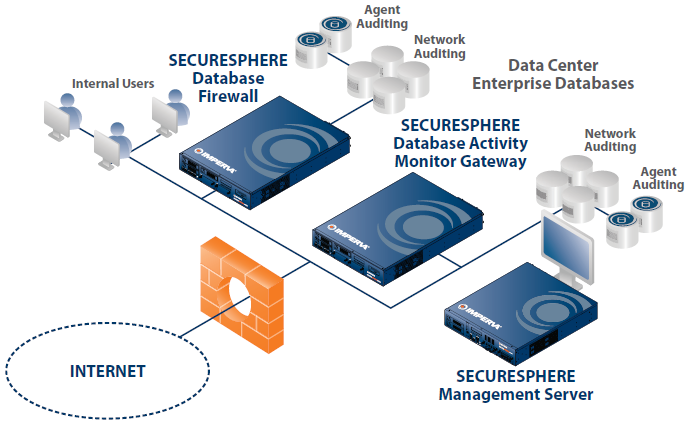
Features and Appliance Specifications:
| Specification | Description |
|---|---|
| Supported Database Platforms |
|
| Automated Discovery |
|
| Data Classification |
|
| Vulnerability Assessment |
|
| Enterprise Application Assessments |
|
| Compliance Assessments |
|
| Risk Management |
|
| Scheduling |
|
| Actions |
|
| Assessment Updates |
|
| Performance Overhead |
|
| Management |
|
| Role-Based Controls |
|
| Event Notification |
|
| Reports |
|
| Report Formats |
|
| Related Products |
Documentation:
Download the SecureSphere Discovery and Assessment Server Datasheet (PDF).
Download the Imperva SecureSphere Database Security Products Datasheet (PDF).
Download the Imperva SecureSphere Appliances Datasheet (PDF).
