
Imperva SecureSphere - Database Activity Monitor
Audit Database Access and Usage of Sensitive Data
Overview:
SecureSphere Database Activity Monitor helps you efficiently demonstrate database compliance through automated processes, audit analysis, and customizable reports across heterogeneous database platforms. In addition, SecureSphere accelerates incident response and forensic investigation with centralized management and advanced analytics. Database Activity Monitor helps you pass your database audits and avoid hefty non-compliance fines.
Database activity monitoring and auditing has become a critical challenge for organizations due to increasing importance of data integrity and privacy to customers and regulators. The need to continuously audit database access, by privileged and non-privileged users, on a large number of databases, is addressed by SecureSphere's automated and scalable database audit solution.
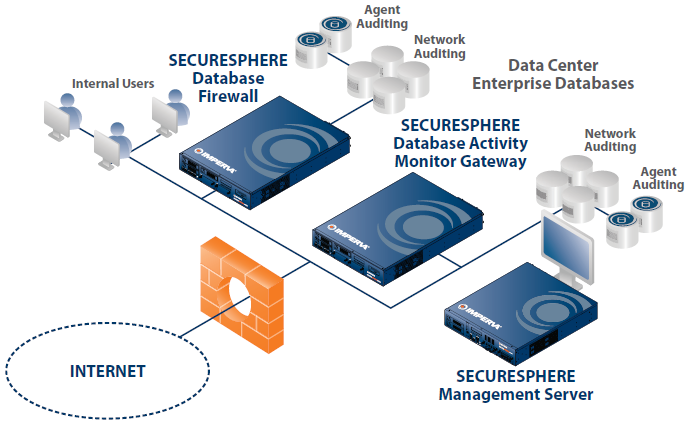
Unique to the industry, SecureSphere enables customers to optimize their DAM implementations by combining agent-based monitoring and network activity monitoring. SecureSphere database agents can be configured for monitoring local privileged activity exclusively, or for monitoring all database activity. SecureSphere's hybrid architecture provides comprehensive database auditing with minimal overhead and unparalleled scalability.

Key Capabilities:
- Continuous audit of all access to sensitive data by privileged and application users
- Alert on abnormal access requests and database attacks, in real time
- Accelerate incident response and forensic investigation through centralized management
and advanced analytics - Provide audit reports to demonstrate compliance with regulatory requirements
- Identify databases and objects in scope for Compliance and Security Projects
Features:
Continuous Auditing of Sensitive Data Usage
SecureSphere continuously monitors and audits all database operations in real time, providing organizations with a detailed audit trail that shows the 'Who, What, When, Where, and How' of each transaction. SecureSphere audits privileged users who directly access the database server, as well as non-privileged users accessing the database through various applications. SecureSphere also monitors the database response to alert or stop leakage of sensitive data.
Audit Analytics for Incident Investigation and Forensics
SecureSphere provides deep insight into audited activities through interactive audit analytics. SecureSphere enables security teams and database auditors to quickly view, analyze, and correlate database activities from virtually any angle from a simple user interface, without requiring any SQL scripting. Interactive audit analytics simplifies forensic investigations and enables identification of trends and patterns that may indicate security risks.
Detection of Unauthorized Access, Fraudulent Activity
SecureSphere identifies normal user access patterns to data using patent-pending Dynamic Profiling technology. It establishes a baseline of all user activity including DML, DDL, DCL, read-only activity (SELECTs), and usage of stored procedures. SecureSphere detects material variances when users perform unexpected queries and alerts or blocks users who violate access policies. Users performing unauthorized SQL requests can also be quarantined until their access rights have been reviewed and approved.
Real-Time Blocking of SQL Injection, DoS, and More
While selectively auditing access to sensitive data, SecureSphere monitors all database activity in real time to detect unknown data leakage, unauthorized SQL transactions, and protocol and system attacks. Whether originating from an application or a privileged user, on the network or on the database server itself, SecureSphere can alert on and optionally block malicious attacks.
Policy Enforcement, Streamlined Compliance Reporting
SecureSphere includes a complete set of predefined, customizable security and audit policies. Out-of-the-box awareness of enterprise applications such as SAP, Oracle EBS, and PeopleSoft and key regulations including SOX, PCI DSS, and HIPAA simplify deployment and time to compliance. Security alerts can be sent to SIEM, ticketing systems, and other third-party solutions to streamline business processes.
Classifying Data in Scope for Compliance and Security
SecureSphere detects all database systems in scope for security and compliance projects through automated discovery and classification of sensitive data. Combining discovery and classification with vulnerability assessment enables organizations to prioritize vulnerability remediation efforts.
Assessment and Virtual Patching of Database Vulnerabilities
Including over fifteen hundred configuration, database, and platform vulnerability assessments, SecureSphere helps organizations identify and remediate vulnerabilities. For immediate protection, SecureSphere Virtual Patching can block attempts to exploit discovered vulnerabilities. Virtual Patching minimizes the window of exposure and drastically reduces the risk of a data breach while testing and deploying database patches.
Effective User Rights Management Across Databases
SecureSphere automatically aggregates user rights across heterogeneous databases. With User Rights Management, organizations can establish an automated process for access rights review, identify excessive user rights, and demonstrate compliance with regulations such as SOX, PCI 7, and PCI 8.5.
Local Database Auditing and Protection Using Lightweight Agents
For complete visibility and control of all user activity, SecureSphere extends its monitoring, auditing, and enforcement capabilities to database servers. Lightweight SecureSphere agents audit database activity and protect sensitive data with minimal impact to server performance.
Unparalleled Database Security and Compliance
SecureSphere addresses all aspects of database security and compliance with industry-best database auditing and real-time protection that will not impact performance or availability. With its multi-tier architecture, SecureSphere scales to support the largest database installations. By automating security and compliance, it is not surprising that thousands of organizations choose Imperva SecureSphere to safeguard their most valuable assets.
Deployment:
Unparalleled Database Security and Compliance
SecureSphere addresses all aspects of database security and compliance with industry-best database auditing and real-time protection that will not impact performance or availability. With its multi-tier architecture, SecureSphere scales to support the largest database installations. By automating security and compliance, it is not surprising that thousands of organizations choose Imperva SecureSphere to safeguard their most valuable assets.
- Non-inline Network Monitoring: Activity monitoring with zero impact on database performance or availability
- Transparent Inline Protection: Drop-in deployment and industry-best performance
- Agent-based Monitoring and Blocking: Lightweight software agents that monitor and block direct privileged activities and network traffic
- Gateway Clustering: Cost-effective resilient database auditing
- Supported Database Platforms: Oracle, Oracle Exadata, Microsoft SQL Server, IBM DB2 (on Linux, UNIX, Windows, z/OS and DB2/400), IBM IMS on z/OS, IBM Informix, IBM Netezza, SAP Sybase, Teradata, Oracle MySQL, PostgreSQL, and Progress OpenEdge
Features and Appliance Specifications:
| Specification | Description |
|---|---|
| Supported Database Platforms |
|
| Deployment Modes |
|
| Performance Overhead |
|
| Centralized Management |
|
| Database Audit |
|
| Privileged Activities |
|
| Access to Sensitive |
|
| Security Exceptions |
|
| Data Modification |
|
| Stored Procedures |
|
| Triggers |
|
| Tamper-Proof Audit Trail |
|
| Fraud Identification |
|
| Data Leak Identification |
|
| Database Security |
|
| Platform Security |
|
| Network Security |
|
| Policy Updates |
|
| Real-Time Event Management and Report distribution |
|
| Server Discovery |
|
| Data Discovery and Classification |
|
| User Rights Management (add-on option) |
|
| Vulnerability Assessment |
|
View Demo:
Documentation:
Download the Imperva SecureSphere Database Security Products Datasheet (PDF).
Download the Imperva SecureSphere Appliances Datasheet (PDF).
