
Imperva SecureSphere - File Firewall
Real-Time Protection Against Improper Access and Data Loss
Overview:
Hackers know what they want and where to find it. Critical data centers such as file servers are targets for your “crown jewels,” like intellectual property, deal data, or PII. Cyber-attacks have become increasingly sophisticated, leveraging multiple tactics and tools, all with one goal: getting in. Imperva adds a tough layer of protection directly around your files so that sensitive data is secure—to prevent breaches, along with the resulting exposure, brand damage, and costs that they bring.
SecureSphere File Firewall (FFW) delivers real-time file security with policy-based alerting and blocking, access activity auditing, and user rights management for files stored on file servers and network attached storage (NAS) devices. SecureSphere policies complement file server access control lists (ACLs) which often fall out of synch with corporate security policy. In addition to blocking unwarranted access, SecureSphere creates a comprehensive file activity audit record which can be used to accelerate security incident response and forensic investigations. SecureSphere FFW helps ensure access to sensitive file data is based on a business need-to-know by identifying existing user access rights and facilitating a complete rights review.

Key Capabilities:
- Identify excessive user access rights and enable a complete file rights audit and review cycle
- Audit all access to files including access by privileged users and applications
- Alert on file access requests that violate corporate policies
- Identify data owners
- Document compliance, investigate and respond to incidents with advanced analytics and reporting
Features:
Control User Access Rights to Sensitive File Data
SecureSphere FAM identifies existing user access rights and facilitates a complete rights review cycle to ensure sensitive file data is accessible only by those with a business need-to-know. It streamlines audits by aggregating, consolidating and reporting on user access rights to file data across all file servers and NAS devices. SecureSphere accelerates review cycles by:
- Identifying users with access to sensitive, high-risk file data
- Highlighting users with excessive access rights
- Discovering dormant users and un-used access rights
- Providing rights review workflow capabilities
Audit all File Data Access
SecureSphere performs continuous monitoring and detailed auditing of all file operations in real-time to provide organizations with a complete audit trail that shows the 'Who, What, When, Where, and How' of each file data access. It monitors network communications and transparently records every user access of file data without impacting applications, users or file servers. SecureSphere creates a detailed audit trail that includes the name of the user, file accessed, parent folder, access operation (e.g., open, read, write, delete, etc.), access time, etc. For maximum security, the audit trail is maintained in an external, secured, and hardened repository which can be accessed exclusively through read-only views via a role based access mechanism.
Identify Owners of Files and Folders
SecureSphere FAM helps in the identification of data owners by providing visibility into the users of files and folders. The primary file and folder users are either the data owners or, as the largest data consumers, are able to immediately identify an owner. Owner identification is critical for compliance, security and IT operations because owners understand the business relevance of their data and can therefore provide critical input on how data should be managed and protected.
Quickly and efficiently document compliance, investigate and respond to incidents
SecureSphere provides interactive, on-screen audit analytics for visualizing file data activity and user rights with just a few clicks. Security, compliance and audit staff can leverage these analytics to identify trends, patterns and problems with file activity and user rights. SecureSphere reporting complements on-screen analytics and helps measure risk and document compliance with regulations such as SOX, PCI, and data privacy laws. For increased efficiency and automation, SecureSphere provides report templates and scheduling.
Alert on Abnormal Activity
SecureSphere FAM detects and alerts on access activity that deviates from corporate policy. Using a flexible framework, administrators can create policies that consider a variety of criteria, such as file meta-data (e.g., name, location, type, etc.), permissions and user access activity, and then take action when undesirable behaviors are observed. For example, an alert policy can be configured to trigger when "Marketing" users access "Financial Data". SecureSphere alerts support a broad range of actions including sending an email to interested parties, assigning a follow-up task to an administrator, or executing an operating system command. Organizations can also establish file data security policies by blocking access with SecureSphere File Firewall.
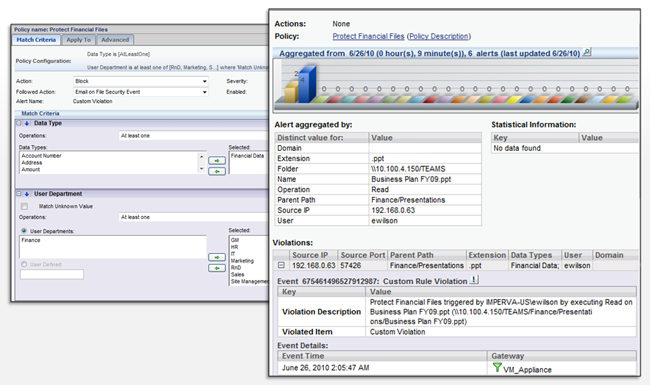
Increase IT Operations Efficiency
SecureSphere helps IT operations staff, such as Windows, storage, help desk and directory services administrators work more efficiently. For example, because SecureSphere creates an audit record of all file access activity, data that is not being accessed can be identified and deleted or archived. Help desk staff can make faster decisions about granting access rights with SecureSphere information about data owners and effective permissions. Data ownership details and information about unused data also expedite data migrations and directory services domain consolidations. Migration and consolidation projects are also a natural time to conduct rights reviews, which User Rights Management for Files dramatically simplifies.
Quickly Put a Stop to Suspicious Activity
Prevent your files from becoming an easy target for internal and external threats. With File Firewall, you can immediately respond to suspicious file access activity by generating notifications, or in certain situations, blocking access completely. With the industry’s leading security policy framework, you can trust that your file data is fully protected.
Incident Details at Your Fingertips
When it comes to security incident response, the sooner the better. Begin investigations right away with immediate access to a record of all file activity across your organization. Uncover all the details in just a few clicks with interactive audit analytics that help you identify suspicious behavior, understand user permissions, and document problems.
Boost Efficiency and Tighten Controls With Automated Access Rights Reviews
To keep data secure, it’s important to continually review file access permissions. With SecureSphere, you can finally put a regular workflow in place for reviewing file access rights. Allow data owners to make access control decisions by including them in your routine review cycles.
Protect Your Data From Advanced Threats
You can’t afford to leave your files exposed to malware and targeted attacks. With Imperva and FireEye, you don’t need to worry. Be confident that your sensitive and regulated data is safe from advanced threats with an added layer of protection around your files, triggered by a leading malware detection system.
Deployment:
Rely on the Leader in Data Security
SecureSphere offers best-of-breed file auditing and user rights management that accelerate compliance, bolster security, and streamline IT operations processes. Leveraging a powerful centralized management and reporting platform, SecureSphere meets the needs of any environment – from small organizations with a single file server to large enterprises with geographically distributed data centers. SecureSphere provides unparalleled data security with protection for Web applications, databases, and files.
Flexible inline and non-inline deployment modes offer easy installation with no changes to file servers, NAS devices, applications, clients, or network
- Non-inline Network Monitoring: Activity monitoring with zero impact on performance or availability
- Transparent Inline Protection: Drop-in deployment and industry-leading performance for proactive security

Specifications:
| Specification | Description |
|---|---|
| Operating Systems Supported |
|
| File Systems Supported |
|
| Directory Services Supported |
|
| User Rights Management |
|
| File System Activity Audit |
|
| Data Classification |
|
| Tamper-Proof Audit Trail |
|
| Deployment Modes |
|
| Management |
|
| Administration |
|
| Events and Reporting |
|
| Related Products |
|
Documentation:
Download the SecureSphere File Security Datasheet (PDF).
